04. Layering Protection
Layering Protection
ND545 C1 L4 03 Layering Protection Video
Layering Protection summary
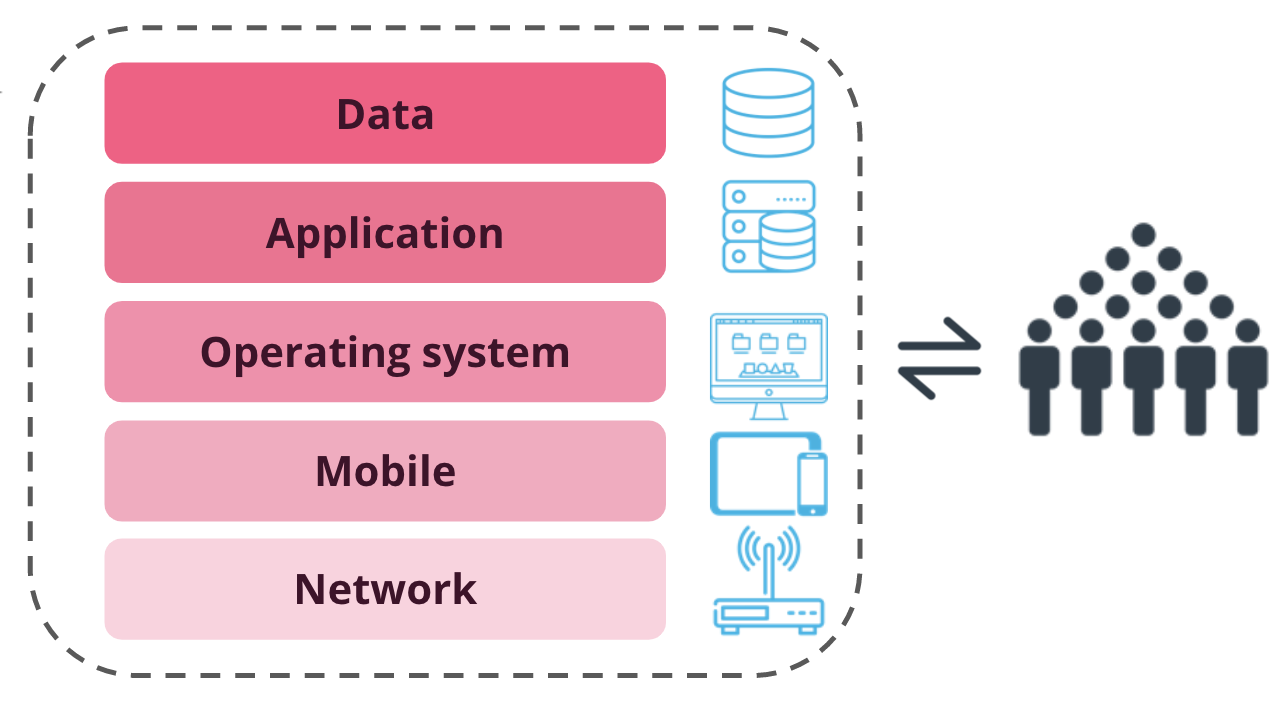
Defense in depth provides multiple layers of protection to our computer systems, networks and data. Computing systems today also use multiple levels.
- Network
- Mobile
- Operating System
- Applications
- Data
Surrounding each of these layers are humans that interact with each layer.
For more information on industry-standard network layering, see the OSI 7-Layer model.
By the end of this lesson, you'll be able to explain how security defenses are layered throughout different system architectures.
Hardening Systems
ND545 C1 L4 04 Layering Protection Walkthrough
Hardening Systems summary
A part of layering security is “hardening” systems. This means applying security settings to protect against attacks, misuse or error.
Rather than creating your own technical security standards, it's better to follow what others are doing. Fortunately, we have a resource for that.
The Center for Internet Security provides benchmark guides for common networking devices, operating systems and applications. These are a target for optimal security on specific technologies and can be used to compare an organization’s systems against those targets.
Their website (https://www.cisecurity.org/cis-benchmarks/) provides over 140 technical guidelines providing best practices for securing a system’s configuration. CIS Benchmarks are distributed free of charge in PDF format.
Examples of benchmarks:
- Desktops & Web Browsers
- Mobile Devices
- Network Devices
- Servers – Operating Systems
- Servers – Other
- Virtualization Platforms & Cloud
As a security and systems administrator, we use these guides to tell us how to harden our systems.
New terms
- **Hardening: **A process intended to eliminate a means of attack by patching vulnerabilities and turning off nonessential services.
Source: https://csrc.nist.gov/glossary/
Further research
- CIS Benchmarks - https://www.cisecurity.org/cis-benchmarks/